CompTIA Network +
What Is CompTIA Network + Certification ?
The N+ which stands for CompTIA Network + is an entry level information technology certification issued by networking company CompTIA. The Network + is designed to validate your knowledge on fundamental networking concepts often requested in networking roles in IT positions.
What Skills CompTIA N+ Develop ?
The following are the abilities you can learn from the CompTIA N+ course:
- Networking Fundamentals
- Internet Protocol Services
- Handle Network Devices
- Device Management
Syllabus:-
- Networking Fundamentals
- Internet Protocol Fundamentals
- Live Practical Workshop
Module : 1
Network Fundamentals
1. Network Device Technology
Network Devices
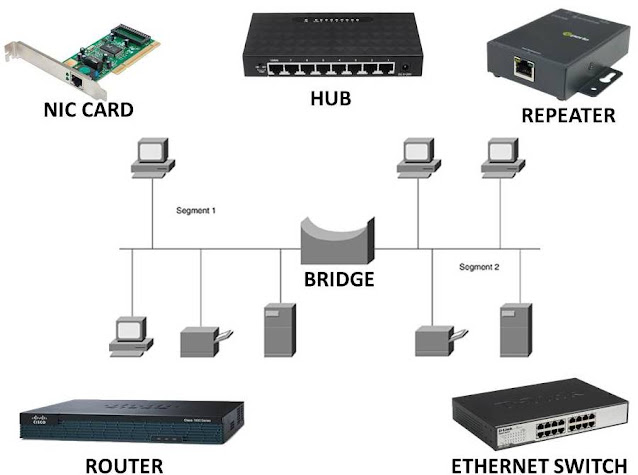
Network devices, also known as networking hardware, are physical devices that allow hardware on a computer network to communicate and interact with one another. For example Repeater, Hub, Bridge, Switch, Routers, Gateway and NIC, etc.
1. Repeater
A repeater operates at the physical layer. Its job is to regenerate the signal over the same network before the signal becomes too weak or corrupted to extend the length to which the signal can be transmitted over the same network. An important point to be noted about repeaters is that they not only amplify the signal but also regenerate it. When the signal becomes weak, they copy it bit by bit and regenerate it at its star topology connectors connecting following the original strength. It is a 2-port device.
2. Hub
A hub is a basically multi-port repeater. A hub connects multiple wires coming from different branches, for example, the connector in star topology which connects different stations. Hubs cannot filter data, so data packets are sent to all connected devices.
3. Bridge
A bridge operates at the data link layer. A bridge is a repeater, with add on the functionality of filtering content by reading the MAC addresses of the source and destination. It is also used for interconnecting two LANs working on the same protocol. It has a single input and single output port, thus making it a 2 port device.
4. Switch
A switch is a multiport bridge with a buffer and a design that can boost its efficiency(a large number of ports imply less traffic) and performance. A switch is a data link layer device. The switch can perform error checking before forwarding data, which makes it very efficient as it does not forward packets that have errors and forward good packets selectively to the correct port only. In other words, the switch divides the collision domain of hosts, but the broadcast domain remains the same.
Types of Switch
- Unmanaged switches: These switches have a simple plug-and-play design and do not offer advanced configuration options. They are suitable for small networks or for use as an expansion to a larger network.
- Managed switches: These switches offer advanced configuration options such as VLANs and link aggregation. They are suitable for larger, more complex networks and allow for centralized management.
- Smart switches: These switches have features similar to managed switches but are typically easier to set up and manage. They are suitable for small- to medium-sized networks.
- Layer 2 switches: These switches operate at the Data Link layer of the OSI model and are responsible for forwarding data between devices on the same network segment.
- Layer 3 switches: These switches operate at the Network layer of the OSI model and can route data between different network segments. They are more advanced than Layer 2 switches and are often used in larger, more complex networks.
- PoE switches: These switches have Power over Ethernet capabilities, which allows them to supply power to network devices over the same cable that carries data.
- Gigabit switches: These switches support Gigabit Ethernet speeds, which are faster than traditional Ethernet speeds.
- Rack-mounted switches: These switches are designed to be mounted in a server rack and are suitable for use in data centers or other large networks.
- Desktop switches: These switches are designed for use on a desktop or in a small office environment and are typically smaller in size than rack-mounted switches.
- Modular switches: These switches have modular design, which allows for easy expansion or customization. They are suitable for large networks and data centers.
5. Routers
A router is a device like a switch that routes data packets based on their IP addresses. The router is mainly a Network Layer device. Routers normally connect LANs and WANs and have a dynamically updating routing table based on which they make decisions on routing the data packets. The router divides the broadcast domains of hosts connected through it.
6. Gateway
A gateway, as the name suggests, is a passage to connect two networks that may work upon different networking models. They work as messenger agents that take data from one system, interpret it, and transfer it to another system. Gateways are also called protocol converters and can operate at any network layer. Gateways are generally more complex than switches or routers. A gateway is also called a protocol converter.
7. Network Interface Card (NIC)
NIC or network interface card is a network adapter that is used to connect the computer to the network. It is installed in the computer to establish a LAN. It has a unique id that is written on the chip, and it has a connector to connect the cable to it. The cable acts as an interface between the computer and the router or modem. NIC card is a layer 2 device which means that it works on both the physical and data link layers of the network model.

A LAN cable is a conductor that connects devices in a Local Area Network (LAN) with a network connector. The network cable provides communication between several devices (computers, routers, switches,…). The term “LAN” is an overtake for Ethernet cable. It is also know as "Twisted Pair Cable".
Categories of UTP Cables:
Category | Bandwidth | Speed | Use |
|---|---|---|---|
1 | 1.4 MHz | 1 Mbps | Telephone wire |
2 | 4 MHz | 4 Mbps | Transmission Lines |
3 | 16 MHz | 16 Mbps | 10BaseT Ethernet |
4 | 20 MHz | 20 Mbps | Used in Token Ring |
5 | 100 MHz | 100 Mbps | 100BaseT Ethernet |
5 | 100 MHz | 1 Gbps | Gigabit Ethernet |
5e | 100 MHz | 1 Gbps | Gigabit Ethernet |
6 | 250 MHz | 10 Gbps | Gigabit Ethernet |
7 | 600 MHz | 10 Gbps | Gigabit Ethernet |
7a | 1 GHz | Up to 10 Gbps | Gigabit Ethernet |
8 | 2 GHz | 25 Gbps to up to 40 Gbps | Datacenters |
3. Open Systems Interconnection Model (OSI Model)
It has 7 layers Physical layer, Data Link layer, Network layer, Transport layer, Session layer, Presentation layer, and Application layer. Each layer performs its task independently. It was developed in 1984 by the International Organization for Standardization (ISO).
Advantages
- Both connection-oriented services and connectionless services are supported.
- It is quite flexible.
- All the layers work independently.
Disadvantages
- Setting up a model is a challenging task.
- Sometimes, it becomes difficult to fit a new protocol into this model.
- It is only used as a reference model.
Advantages
- Many Routing protocols are supported.
- It is highly scalable and uses a client-server architecture.
- It is lightweight.
Disadvantages
- Little difficult to set up.
- Delivery of packets is not guaranteed by the transport layer.
- Vulnerable to a synchronization attack.
Difference Between OSI Model & TCP/IP Model
| Parameter | OSI Model | TCP/IP Model |
|---|---|---|
| Full Form | OSI stands for Open Systems Interconnection. | TCP/IP stands for Transmission Control Protocol/Internet Protocol. |
| Layers | It has 7 layers. | It has 4 layers. |
| Usage | It is low in usage. | It is mostly used. |
| Approach | It is vertically approached. | It is horizontally approached. |
| Delivery | Delivery of the package is guaranteed in OSI Model. | Delivery of the package is not guaranteed in TCP/IP Model. |
| Replacement | Replacement of tools and changes can easily be done in this model. | Replacing the tools is not easy as it is in OSI Model. |
Reliability | It is less reliable than TCP/IP Model. | It is more reliable than OSI Model. |
5. Data Encapsulation and Decapsulation
Data Encapsulation
Sending and receiving of data from a source device to the destination device is possible with the help of networking protocols by using data encapsulation. When a host transmits data to another device across a network, the data is encapsulated with protocol information at each layer of the OSI reference model. Each layer communicates with its neighbor layer on the destination. Each layer uses Protocol Data Units (PDUs) to communicate and exchange information.
Protocol Data Unit (PDU)
The Protocol Data Units contain the control information attached to the data at each layer. The information is attached to the header of the data field but can also be in end of the data field or trailer. PDUs are encapsulated by attaching them to the data at each layer of the OSI reference model. Each Protocol Data Unit has a name depending on the information each header has. This PDU information is only read by the neighbor layer on the destination and then is stripped off and the data is handed to the next layer.
OSI Layer Model and PDUs
The seven layered Open System Interconnection (OSI) model is basically defined for reducing the complexity of the internetworking. The OSI Model is then divided into two segments for more ease, Upper layers and Data Flow layers. The 7th, 6th and 5th layer of the OSI reference model are application layers also known as upper layers. The upper layers are directly related with user interface while the 4rth, 3rd, 2nd and 1st layer of the OSI model are also called data flow layers because they are related with the flow of the data. Each data flow layer has a Protocol Data Unit.
Protocol Data Unit of each data flow layers is defined as follows:
Transport Layer: Segment is the PDU of the Transport layer.
Network Layer: Packet is the PDU of the Transport layer.
Data Link Layer: Frame is the PDU of the Transport layer.
Physical Layer: Bit is the PDU of the Transport layer.
The encapsulation and de-encapsulation of header control information on each layer of the OSI reference model is as follows:
The application-layers user data is converted for transmission on the network. The data stream is then handed down to the Transport layer, which sets up a virtual circuit to the destination. The data stream is then broken up, and a Transport layer header is created and called a segment. The header control information is attached to the Transport layer header of the data field. Each segment is sequenced so the data stream can be put back together on the destination exactly as transmitted.
IP Header Encapsulation
Each segment is then handed to the Network layer for logical addressing and routing through a routed protocol, for example IP, IPX, Apple Talk and DECNET etc. The Network-layer protocol adds a header to the segment handed down to the Data Link layer. Remember that the 3rd and 4rth layers work together to rebuild a data stream on a destination host. However, they have no responsibility for placing their Protocol Data Units on a local network segment, which is the only way to get the information to host or router.
MAC Header Encapsulation
The Data Link layer receives the packets from the Network layer and placing them on the network medium such as cable or wireless media. The Data Link layer encapsulates each packet in a frame, and the MAC header carries the source Mac address and destination Mac address. If the device is on a different network, then the frame is sent to a router to be routed through an internetwork.
Physical Layer Encapsulation
Once the frame gets to the destination network, a new frame is used to get the packet to the destination host. To put this frame on the network, it must first be put into a digital signal. Since a frame is really a logical group of 1s and 0s, the Physical layer of the OSI model is responsible for encapsulating these digits into a digital signal, which is read by devices on the same local network.
Data Encapsulation Flow
At a transmitting device, the data encapsulation method works as follows: User information is converted into data for transmission on the network. Data is converted into segments and a reliable or unreliable connection is set up between the source and destination devices using connection oriented and connectionless protocols. Segments are converted into packets using a logical address such as IP datagram using an IP address. Packets are converted into frames for transmission on the local network. Media Access Control (MAC) addresses or Ethernet addresses are commonly used to uniquely identify hosts on a local network segment. Frames are converted into bytes and bits, and a digital encoding and clocking or signaling method is used.
De-Encapsulation Flow
On destination side, the receiving devices will synchronize on the digital signal and extract the 1s and 0s from the digital signal. At this point the devices build the frames, run a Cyclic Redundancy Check (CRC), and then check their output against the output in the Frame Check Sequence (FCS) field of the data frame. If the information matches then the packet is pulled from the frame, and the frame is discarded. This process is known as de-encapsulation. The packet then transfers to the Network layer, where the IP address is checked. If the IP address matches then the segment is pulled from the packet, and the packet is discarded. The data is processed at the Transport layer that rebuilds the data stream and acknowledges to the transmitting station that it received each piece of segment. It then happily transfers the data stream to the upper layer application.
Broadcast Domain
The definition of a broadcast domain is a set of devices that if one device sends a broadcast frame, all other devices will receive that frame in the same broadcast domain. So if devices are in the same IP network, they will be able to receive a broadcast message. Having a smaller broadcast domain can improve network performance and improve against security attacks. The more PCs and network devices connected to a single broadcast domain, the more broadcast messages you will have. Remember a broadcast message goes to every PC and network device.
Collision Domain
Collision domain is a set of LAN devices whose frames could collide with one another. This happens with hubs, bridges, repeaters and wireless access points as only one device can send and receive at a time. If more than one device tries sending or receiving, the information is lost and irrecoverable and it will need to be resent. This can slow down network performance along with making it a security threat. A hub is considered a layer one device of the OSI model; all it does is send packets out on all ports including the port in which the packet was received on. This causes a collision because only one device can transmit at time. This also shares the bandwidth of all devices connected to that collision domain All the devices are connected to a hub in this diagram. When two pcs send data at the same time, there can be a collision so the number of collision domain of hub is one.
1. Internet Protocol (IP) Address
An internet protocol address is an numerical label assigned to each device connected to a computer network that uses the internet protocol for communication an ip address serves two basic principle functions.
Rule:- Host and network interface identification location addressing.
IP address determines who and where you are in the network of billions of digital devices that are connected to the Internet.
IP address is your digital identity. It’s a network address for your computer so the Internet knows where to send you emails, data, etc.
Part of IPv4
- Network Part:The network part indicates the distinctive variety that’s appointed to the network. The network part conjointly identifies the category of the network that’s assigned.
- Host Part:The host part uniquely identifies the machine on your network. This part of the IPv4 address is assigned to every host.For each host on the network, the network part is the same, however, the host half must vary.
- Subnet Number:This is the nonobligatory part of IPv4. Local networks that have massive numbers of hosts are divided into subnets and subnet numbers are appointed to that.
Classification of IPv4
Within each network class, there are designated IP address that is reserved specifically for private/internal use only. This IP address cannot be used on Internet-facing devices as that are non-routable. For example, web servers and FTP servers must use non-private IP addresses. However, within your own home or business network, private IP addresses are assigned to your devices (such as workstations, printers, and file servers).
- Class A Private Range: 10.0.0.0 to 10.255.255.255
- Class B Private APIPA Range: 169.254.0.0 to 169.254.255.255
- Automatic Private IP Addressing (APIPA) is a feature with Microsoft Windows-based computers to automatically assign itself an IP address within this range if a Dynamic Host Configuration Protocol (DHCP) server is not available on the network. A DHCP server is a network device that is responsible for assigning IP addresses to devices on the network.
- At your home, your Internet modem or router likely provides this functionality. In your work place, a Microsoft Windows Server, a network firewall, or some other specialized network device likely provides this functionality for the computer at your work environment.
- Class B Private Range: 172.16.0.0 to 172.31.255.255
- Class C Private Range: 192.168.0.0 to 192.168.255.255
Public IP Address is basically of two types:
- Dynamic IP Address: Dynamic IP Addresses are addresses that change over time. After establishing a connection of a smartphone or computer with the Internet, ISP provides an IP Address to the device, these random addresses are called Dynamic IP Address.
- Static IP Address: Static Addresses are those addresses that do not change with time. These are stated as permanent internet addresses. Mostly these are used by the DNS (Domain Name System) Servers.
Difference Between Private & Public IP Address
Private IP Address Public IP Address The scope of Private IP is local. The scope of Public IP is global. It is used to communicate within the network. It is used to communicate outside the network. Private IP addresses of the systems connected in a network differ in a uniform manner. Public IP may differ in a uniform or non-uniform manner. It works only on LAN. It is used to get internet service. It is used to load the network operating system. It is controlled by ISP. It is available free of cost. It is not free of cost. Private IP can be known by entering “ipconfig” on the command prompt. Public IP can be known by searching “what is my ip” on Google. Range:
10.0.0.0–10.255.255.255
172.16.0.0–172.31.255.255
192.168.0.0–192.168.255.255
Range: Besides private IP addresses, the rest are public. Example: 192.168.1.10 Example: 17.5.7.8 Private IP uses numeric code that is not unique and can be used again. Public IP uses a numeric code that is unique and cannot be used by other. Private IP addresses are secure. The public IP address has no security and is subjected to attack. Private IP addresses require NAT to communicate with devices. Public IP does not require a network translation.
| Private IP Address | Public IP Address |
|---|---|
| The scope of Private IP is local. | The scope of Public IP is global. |
| It is used to communicate within the network. | It is used to communicate outside the network. |
| Private IP addresses of the systems connected in a network differ in a uniform manner. | Public IP may differ in a uniform or non-uniform manner. |
| It works only on LAN. | It is used to get internet service. |
| It is used to load the network operating system. | It is controlled by ISP. |
| It is available free of cost. | It is not free of cost. |
| Private IP can be known by entering “ipconfig” on the command prompt. | Public IP can be known by searching “what is my ip” on Google. |
Range:
| Range: Besides private IP addresses, the rest are public. |
| Example: 192.168.1.10 | Example: 17.5.7.8 |
| Private IP uses numeric code that is not unique and can be used again. | Public IP uses a numeric code that is unique and cannot be used by other. |
| Private IP addresses are secure. | The public IP address has no security and is subjected to attack. |
| Private IP addresses require NAT to communicate with devices. | Public IP does not require a network translation. |
Classes of IPv4 Address
The list below shows the five available IP classes, along with the number of networks each can support and the maximum number of hosts (devices) that can be on each of those networks. The four octets that make up an IP address are conventionally represented by A,B,C - such as 127.10.20.30
Additionally, information is also provided on private addresses and loop address (used for network troubleshooting).
Summary of IPv4 Classes
| IP Class | Public IP Range | Private IP Range | Subnet Mask | No. of Networks | No. of Hosts |
|---|---|---|---|---|---|
| Class A | 1.0.0.0 to 127.0.0.0 | 10.0.0.0 to 10.255.255.255 | 255.0.0.0 | 126 | 16,777,214 |
| Class B | 128.0.0.0 to 191.255.0.0 | 172.16.0.0 to 172.31.255.255 | 255.255.0.0 | 16,382 | 65,534 |
| Class C | 192.0.0.0 to 223.255.255.0 | 192.168.0.0 to 192.168.255.255 | 255.255.255.0 | 2,097,150 | 254 |
Class A Public & Private IP Address Range
Class A addresses are for networks with large number of total hosts. Class A allows for 126 networks by using the first octet for the network ID. The first bit in this octet, is always zero. The remaining seven bits in this octet complete the network ID. The 24 bits in the remaining three octets represent the hosts ID and allows for approximately 17 million hosts per network. Class A network number values begin at 1 and end at 127.
- Public IP Range: 1.0.0.0 to 127.0.0.0
- First octet value range from 1 to 127
- Private IP Range: 10.0.0.0 to 10.255.255.255
- Subnet Mask: 255.0.0.0 (8 bits)
- Number of Networks: 126
- Number of Hosts per Network: 16,777,214
Class B Public & Private IP Address Range
Class B addresses are for medium to large sized networks. Class B allows for 16,384 networks by using the first two octets for the network ID. The first two bits in the first octet are always 1 0. The remaining six bits, together with the second octet, complete the network ID. The 16 bits in the third and fourth octet represent host ID and allows for approximately 65,000 hosts per network. Class B network number values begin at 128 and end at 191.
- Public IP Range: 128.0.0.0 to 191.255.0.0
- First octet value range from 128 to 191
- Private IP Range: 172.16.0.0 to 172.31.255.255
- Subnet Mask: 255.255.0.0 (16 bits)
- Number of Networks: 16,382
- Number of Hosts per Network: 65,534
Class C Public & Private IP Address Range
Class C addresses are used in small local area networks (LANs). Class C allows for approximately 2 million networks by using the first three octets for the network ID. In a class C IP address, the first three bits of the first octet are always 1 1 0. And the remaining 21 bits of first three octets complete the network ID. The last octet (8 bits) represent the host ID and allows for 254 hosts per network. Class C network number values begins at 192 and end at 223.
- Public IP Range: 192.0.0.0 to 223.255.255.0
- First octet value range from 192 to 223
- Private IP Range: 192.168.0.0 to 192.168.255.255
- Subnet Mask: 255.255.255.0 (24 bits)
- Number of Networks: 2,097,150
- Number of Hosts per Network: 254
Class D IP Address Range
Class D IP addresses are not allocated to hosts and are used for multicasting. Multicasting allows a single host to send a single stream of data to thousands of hosts across the Internet at the same time. It is often used for audio and video streaming, such as IP-based cable TV networks. Another example is the delivery of real-time stock market data from one source to many brokerage companies.
- Range: 224.0.0.0 to 239.255.255.255
- First octet value range from 224 to 239
- Number of Networks: N/A
- Number of Hosts per Network: Multicasting
Class E IP Address Range
Class E IP addresses are not allocated to hosts and are not available for general use. These are reserved for research purposes.
- Range: 240.0.0.0 to 255.255.255.255
- First octet value range from 240 to 255
- Number of Networks: N/A
- Number of Hosts per Network: Research/Reserved/Experimental
Special IP Address Range
IP Range: 127.0.0.1 to 127.255.255.255 are network testing addresses (also referred to as loop-back addresses). These are virtual IP address, in that they cannot be assigned to a device. Specifically, the IP 127.0.0.1 is often used to troubleshoot network connectivity issues using the ping command. Specifically, it tests a computer's TCP/IP network software driver to ensure it is working properly.
Characteristics of IPv4
- IPv4 could be a 32-Bit IP Address.
- IPv4 could be a numeric address, and its bits are separated by a dot.
- The number of header fields is twelve and the length of the header field is twenty.
- It has Unicast, broadcast, and multicast style of addresses.
- IPv4 supports VLSM (Virtual Length Subnet Mask).
- IPv4 uses the Post Address Resolution Protocol to map to the MAC address.
- RIP may be a routing protocol supported by the routed daemon.
- Networks ought to be designed either manually or with DHCP.
- Packet fragmentation permits from routers and causing host.
Advantage of IPv4
- IPv4 security permits encryption to keep up privacy and security.
- IPV4 network allocation is significant and presently has quite 85000 practical routers.
- It becomes easy to attach multiple devices across an outsized network while not NAT.
- This is a model of communication so provides quality service also as economical knowledge transfer.
- IPV4 addresses are redefined and permit flawless encoding.
- Routing is a lot of scalable and economical as a result of addressing is collective more effectively.
- Data communication across the network becomes a lot of specific in multicast organizations.
- Difficult to feature support for future desires as a result of adding it on is extremely high overhead since it hinders the flexibility to attach everything over IP.
- Security features are nonobligatory.
- IPv4 has high System Management prices and it’s labor-intensive, complex, slow & frequent to errors.
- Internet Routing is inefficient in IPv4.
- Limits net growth for existing users and hinders the use of the net for brand new users.
Types of IPv6
Now that we know about what is IPv6 address let’s take a look at its different types.
- Unicast addresses It identifies a unique node on a network and usually refers to a single sender or a single receiver.
- Multicast addresses It represents a group of IP devices and can only be used as the destination of a datagram.
- Anycast addresses It is assigned to a set of interfaces that typically belong to different nodes.
Advantage of IPv6
- Faster Speeds: IPv6 supports multicast rather than broadcast in IPv4.This feature allows bandwidth-intensive packet flows (like multimedia streams) to be sent to multiple destinations all at once.
- Stronger Security: IP Security, which provides confidentiality, and data integrity, is embedded into IPv6.
Disadvantage of IPv6
- Conversion: Due to widespread present usage of IPv4 it will take a long period to completely shift to IPv6.
- Communication: IPv4 and IPv6 machines cannot communicate directly with each other. They need an intermediate technology to make that possible.
2. Static and Dynamic IP Addresses
ISPs (Internet service providers) assign an IP address to each device on their network. The IP address can be static or dynamic.

Static IP Addresses
A static IP address is an IP address that always stays the same. If you have a web server, FTP server, or other Internet resource that must have an address that cannot change, you can get a static IP address from your ISP. A static IP address is usually more expensive than a dynamic IP address, and some ISPs do not supply static IP addresses. You must configure a static IP address manually.
Dynamic IP Addresses
A dynamic IP address is an IP address that an ISP lets you use temporarily. If a dynamic address is not in use, it can be automatically assigned to a different device. Dynamic IP addresses are assigned using either DHCP or PPPoE.
About DHCP
Dynamic Host Configuration Protocol (DHCP) is an Internet protocol that computers on a network use to get IP addresses and other information such as the default gateway. When you connect to the Internet, a computer configured as a DHCP server at the ISP automatically assigns you an IP address. It could be the same IP address you had before, or it could be a new one. When you close an Internet connection that uses a dynamic IP address, the ISP can assign that IP address to a different customer.
You can configure your Firebox as a DHCP server for networks behind the device. You assign a range of addresses for the DHCP server to use.
About PPPoE
Some ISPs assign IP addresses through Point-to-Point Protocol over Ethernet (PPPoE). PPPoE adds some of the features of Ethernet and PPP to a standard dial-up connection. This network protocol allows the ISP to use the billing, authentication, and security systems of their dial-up infrastructure with DSL modem and cable modem products.








Comments
Post a Comment